
Rotate Secrets Everywhere.
Break Nothing.
You know it’s essential to rotate non-human identity (NHI) credentials – including API keys, certificates, and tokens.
SOC 2, PCI 4 and other regulations require this rotation. As does good security hygiene
But until now this has been a difficult, time-consuming, expensive and risky manual process, leading to NHIs being a factor in 84% of data breaches today
Introducing External Secrets Enterprise
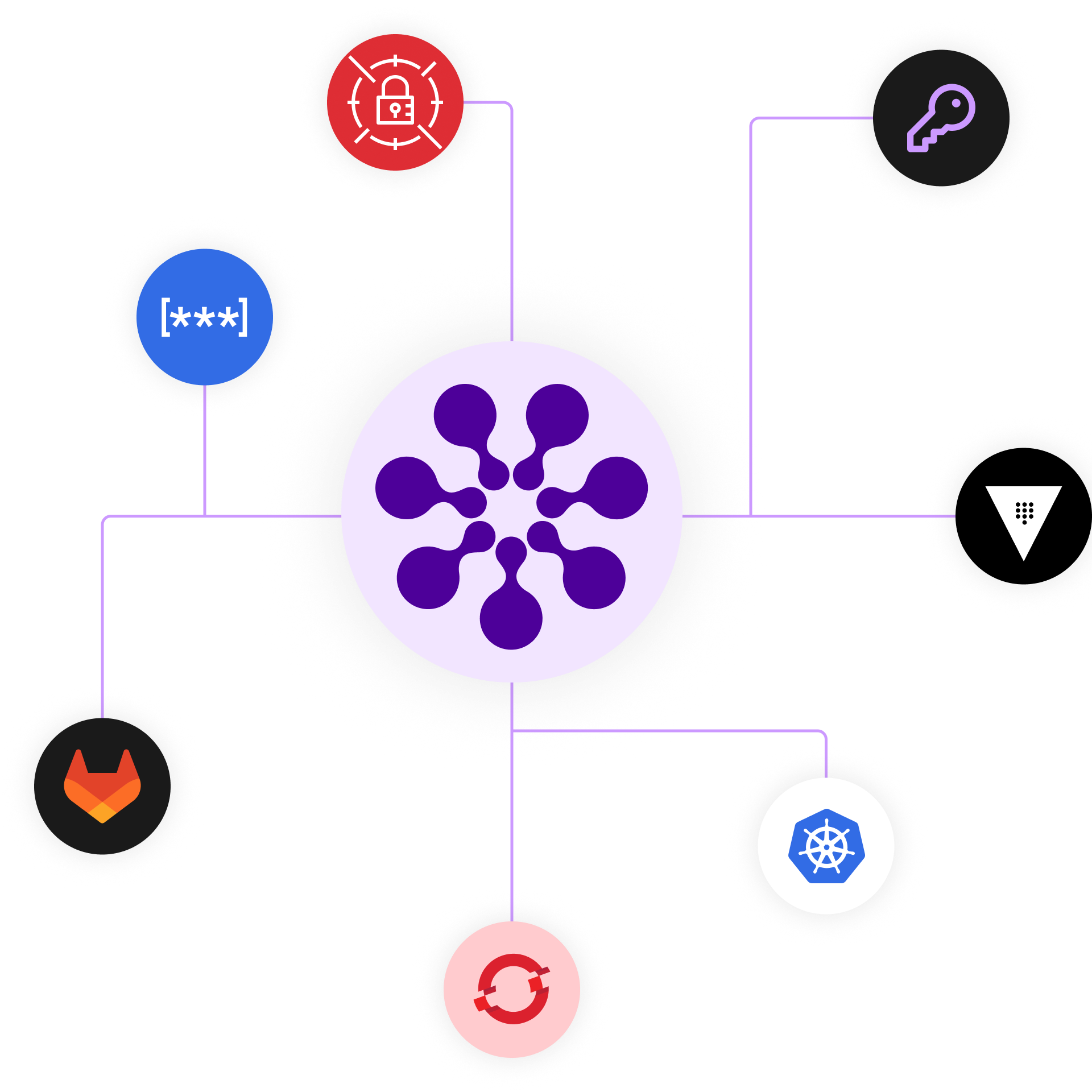
External Secrets is the transport layer for NHI credentials.
We ensure every credential gets where it’s needed, stays in sync, and is rotated on demand or on schedule – all with ZERO breakage or downtime.
We do that securely, comprehensively, and quickly – dramatically lowering costs and headaches of credential rotation.
Why You Need a Credential Transport Layer
Elevate NHI credential access and security through our innovative transport layer that integrates with your existing vault.

Transform Your Security Framework
The unique innovation External Secrets bring to your infrastructure is the provision, for the first time, of a transport layer for your NHI credentials.

Integration with Existing Vaults
You already have a “Vault” to store your passwords and credentials. We work hand-in-glove with every leading Vault on the market. (We don’t store credentials.)

Dynamic Credential Synchronization
Our transport layer distributes those credentials to every client that needs them – and we stay aware of any changes to make sure the clients, server, and vault stay fully synchronized on the latest, most secure set of credentials.
External Secrets:
The Original Credentials Transport Layer
Through both our open-source and enterprise (open-core) products, we are the trusted leader in credentials posture management.

5K+
deployments worldwide

50%
of the Fortune 500 use External Secrets

30+
key vault integrations

24/7
enterprise support for all our products
What you don’t Know can hurt you
Get a free, customized credential posture report
For a limited time, External Secrets is offering a detailed analysis of the enterprise credential landscape for select, qualified enterprises—for free.
Gain a detailed, prioritized look at specific actions you can take to improve your credential posture management. No changes are needed to any part of your existing credential systems and no sensitive data is sent outside your organization.
Stay on top of security with more visibility
Keep secrets up to date and secure
Automate access & rotation management
Meet security and compliance standards
Synchronize secrets to avoid duplicates
Stay on top of security with more visibility
Keep secrets up to date and secure
Automate access & rotation management
Meet security and compliance standards
Synchronize secrets to avoid duplicates
Manage secrets at scale
Handling secrets manually doesn’t scale—especially as your environments grow and security requirements evolve. External Secrets automates secret distribution, rotation, and synchronization across platforms, ensuring seamless management whether you’re handling thousands or millions of secrets.
Easy distribution across environments
No more manual secret management—automate secure distribution to cloud platforms, Kubernetes clusters, and on-prem systems. With seamless integration, secrets are provisioned and updated wherever they’re needed, ensuring consistency and reliability.
Real-time synchronization to keep secrets up to date
Ensure your secrets are always current with real-time synchronization across all systems. Whether a secret changes in a vault, cloud provider, or internal store, updates propagate instantly to prevent outdated or mismatched credentials from causing failures.
Automatic secret rotation and expiration
Eliminate security risks from stale or compromised credentials with automated secret rotation and expiration. Our system seamlessly updates secrets across all environments without breaking applications, reducing the need for manual intervention and improving overall security hygiene.
Compliance enforcement with automated checks & policies
Stay audit-ready with built-in compliance checks that enforce security best practices. Define policies for secret rotation, access, and duplication using industry standards like OPA Rego, and get alerts on non-compliance before it becomes a security issue.
.png)





.svg)

.svg)
%20(1).svg)
.svg)